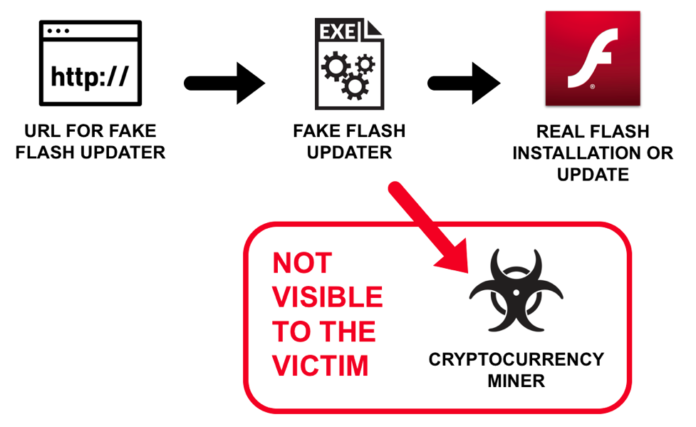
New analysis published by Palo Alto Networks has found that hackers have begun to impersonate Flash update pop-up notifications borrowed from the official Adobe installer to dupe unsuspecting victims into downloading cryptojacking malware. The fake Flash updates are installing unwanted programs like XMRig cryptocurrency miner, in addition to the latest update of Adobe Flash Player.
Cryptojacking malware typically runs as a background application, with victims typically never knowing they have been hacked. Disguised auto-update malware infections are typically considered inelegant and easily detectable. However, this latest iteration is proving to be noticeably more effect.
“Because of the legitimate Flash update, a potential victim may not notice anything out of the ordinary,” writes Unit 42’s Brad Duncan for the research center of Palo Alto Networks. “Meanwhile, an XMRig cryptocurrency miner or other unwanted program is quietly running in the background of the victim’s Windows computer.”
Dunkin continues:
“While searching for these particular fake Flash updates, we noticed Windows executables file names starting with AdobeFlashPlayer__ from non-Adobe, cloud-based web servers. These downloads always contained the string flashplayer_down.php?clickid= in the URL. We found 113 examples of malware meeting these criteria since March 2018 in AutoFocus. 77 of these malware samples are identified with a CoinMiner tag in AutoFocus. The remaining 36 samples share other tags with those 77 CoinMiner-related executables.”
The number of victims arriving at these psudedo-legitimate URLs still remains unclear. While organizations with secure web filtering and educated users have a much lower risk of infection, the vast majority of users are likely to be in danger.
Suggested Reading : Learn more about Monero mining.
Browsers Fighting Back
Cryptojacking continues to be a persistent problem, but mainstream Internet browsing platforms are beginning to fight back. Last month, Firefox announced that its upcoming release would include features to block hidden ‘tracking’ activity plus a cryptojacking blocker. Opera and Brave Browser are also taking similar measures to fight crypto malware.
Further support is beginning to come from a mysterious botnet designed to seek and destroy undetected instances of cryptojacking malware on the internet. The malware-fighting botnet was first discovered by researchers at Qihoo 360Netlab, who explain that the bot scans the web for a specific mining malware called com.ufo.miner. Once detected, the Fbot installs itself on top of the malware and self destructs, taking the malware out with it.
For the latest cryptocurrency news, join our Telegram!

Unhashed.com is author of this content, TheBitcoinNews.com is is not responsible for the content of external sites.
Our Social Networks: Facebook Instagram Pinterest Reddit Telegram Twitter Youtube











