Mining malware may now be painfully familiar to anyone with even a passing awareness of cryptocurrency, but so far businesses and consumers alike are failing to significantly curb its growing threat.
On May 14, Israeli cybersecurity firm Check Point released its latest Global Threat Index, and for the fifth consecutive month it found that the Coinhive crypto-miner is the “most prevalent malware” in the world, affecting 16 percent of organizations globally.
Meanwhile, Santa Clara-based Malwarebytes released its Cybercrime tactics and techniques: Q1 2018 report on April 9, finding that businesses had seen a 27 percent increase in mining malware in the first three months of the year compared to the previous three.
However, while the year-on-year growth in the value of cryptocurrencies would indicate that mining malware is going to continue spreading in parallel, there are some emerging signs that organizations at least are coming to terms with the threat posed by malware.
Exploiting basic vulnerabilities
Check Point’s latest report is more worrying than its headline alone would suggest. Not only does Coinhive – a Javascript malware designed to mine Monero (XMR) – occupy the top spot on April’s list of the ten “most wanted” malware, but second place is taken by Cryptoloot, another stealthy, undetectable miner of XMR. Similar to Coinhive, Cryptoloot has been around for several months, having entered the top ten in December 2017, when Coinhive first claimed the number one spot.
Perhaps more worrying are the means by which mining malware such as Coinhive and Cryptoloot are gaining footholds in IT systems. According to Check Point, hackers are increasingly zoning in on more basic vulnerabilities, such as unpatched bugs in Microsoft Windows Server 2003 and in Oracle Web Logic. Maya Horowitz, Check Point’s Threat Intelligence Group Manager, explained:
“With cryptomining malware’s consistent growth, cyber-criminals are innovating their techniques in order to find new ways to exploit victims’ machines and net more revenue. Now that they’re seeking to infiltrate networks using unpatched server vulnerabilities, this is a clear reminder to organizations that security basics – such as patching – are critical to ensuring that networks remain secure.”
46 percent of the organizations Check Point surveyed had been attacked in April as a result of the Microsoft Windows Server 2003 vulnerability, while 40 percent had been hit because of the Oracle Web Logic flaw. According to Horowitz: “It is troubling that so many organizations were impacted by these known vulnerabilities, especially as patches for both have been available for at least 6 months.”
Growth that benefits from relatively low risk
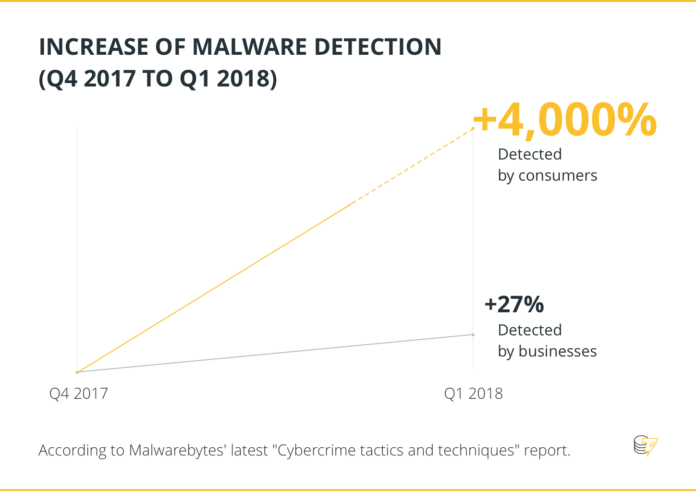
In other words, hackers are using known malware to exploit known vulnerabilities, yet despite the familiarity of their methods organisations appear unable or unwilling to do much to guard themselves against the likes of Coinhive and Cryptoloot. It’s largely for this reason that the detection of malware by businesses increased by 27 percent between Q4 2017 and Q1 2018, according to Malwarebytes’ latest “Cybercrime tactics and techniques” report, underlining the extent to which firms have been caught napping by the cryptojacking wave – for consumers the increase was 4,000 percent.
What’s interesting about such growth is that, as Malwarebytes notes in the report, “virtually all other malware is on the decline.” For example, it finds that the detection of ransomware among consumers declined by 35 percent between Q4 2017 and Q1 2018, while “the overall volume remains low” for business detections of such malware. For example, it was just under 6,000 in March, while mining malware detections were at a hefty 400,000.
Similarly, while spyware is still classed by Malwarebytes as the number one threat for businesses, numbers were relatively low in Q1 2018, with January’s peak of 80,000 detections paling in significance to the 550,000 detections in February for cryptojacking malware.
More interestingly, the report highlights a reason as to why businesses and consumers may not be doing all that much to prevent exposure to mining malware. In its conclusion, it states:
“Malicious cryptomining appears to be far less dangerous to the user than other forms of malware, such as ransomware.”
Indeed, as Yotam Gutman, the Marketing VP at Israeli cybersecurity firm SecuriThings, explains to Cointelegraph:
“Mining consumes CPU and bandwidth. The malware should not harm the host machine, nor should it [impact] the data on the machine – like corrupted or encrypted files. Infected machines tends to work slower, and display higher than usual CPU, power and bandwidth consumption.”
“Most malware mines in a subtle manner, as to not raise any suspicion,” he continues, while it’s worth noting that malware such as Coinhive often stops using a host’s spare processing power if they navigate away from an infected website or close their browser. What’s more, even if organizations or individuals are aware of a possible cryptojacking threat, they may not be moved enough to actually do anything:
“Others are aware that this may happen but are not concerned, what could be the risk of malware that does not steal anything?”
Cryptojacking demand outweighs cybersecurity demand
Given that mining malware generally poses little in the way of an urgent risk, it’s highly likely that its incidence will continue growing in the near future. On one hand, the incentive for businesses and consumers to protect themselves against it isn’t as great as that for adware, spyware or ransomware. On the other, the incentive to mine cryptocurrency illicitly – especially when legitimate mining costs are so high – is considerably large, and will remain so for as long as cryptocurrencies such as XMR maintain or increase their respective values.
Matt Walmsley, the head of EMEA marketing at AI-based cybersecurity firm Vectra, explains to Cointelegraph:
“There is a pattern between the value of cryptocurrencies and the amount of cryptojacking that occurs. For example, we detected that as the value of cryptocurrencies like Bitcoin, Ethereum and Monero increased, there was a corresponding uptick in the number of computers on university campuses performing mining or being cryptojacked by miners to process cryptocurrency hashes.”
Such a correlation paints a bleak picture, since even if mining malware isn’t especially damaging when conducted on a smaller scale, it isn’t without risks for larger organisations and servers. “Devices that are cryptojacked today may be diverted to run more destructive payloads like ransomware, or targeted data theft attacks,” Walmsley says. “The ‘noise’ generated by these low level security events also provides cover for more targeted advanced attacks to hide within. So, organizations that ignore cryptojacking, considering it as just a tolerable low-level security hygiene issue, may be bitten by their complacency when cybercriminals escalate their attacks.”
Tentative signs of improvement
The threat is therefore serious, yet despite the fact that Coinhive is celebrating its fifth consecutive month as Check Point’s “most wanted” malware, there are some tentative signs that organizations are incrementally learning how to deal with it.
For one, even though Check Point found that a significant 16 percent of organizations globally were affected by Coinhive in April, this percentage is in fact lower than that for every preceding month. In January, February, March and April, the malware impacted 23 percent, 20 percent, 18 percent and 16 percent of organizations respectively, while the impact of cryptojacking malware overall declined from 55 percent in December to 42 percent in February.

Businesses are therefore slowly getting a grip on mining malware, a fact also indicated by the very increase in detections recorded by Malwarebytes. The keyword here is “detections” since it may not be the overall deployment or attempted use of mining malware that’s increasing, but rather the ability of organizations to detect such malware when they’re targeted by it – the ‘recorded’ versus ‘actual’ crime conundrum.
However, against these flickers of hope, analysts and cybersecurity researchers would caution that hackers are almost always finding new targets for their malware and new ways of targeting them. Yotam Gutman warns:
“For what we can tell, [the threat] is not slowing down but only growing. Moreover, criminals are finding new computing devices to use – such as IoT devices, so their potential target bank only grows. So sadly, the answer is no, there is no end to crypto mining in sight.”
The prediction that ‘Internet-of-Things’ (IoT) devices will be increasingly targeted as hackers shift their strategies has been made by other experts, with Symantec’s latest Internet Security Threat report forecasting:
“As malicious coin mining evolves, IoT devices will continue to be ripe targets for exploitation. Symantec already found a 600 percent increase in overall IoT attacks in 2017, which means that cyber criminals could exploit the connected nature of these devices to mine en masse.”
Given that hackers have recently been able to move from one basic server vulnerability to the next in their hunt for ill-gotten cryptocurrency, there’s every reason to suspect that they’ll continue moving to IoT devices and other easy targets as and when these emerge. Coupled with the solid performance of cryptocurrency markets, there’s no reason to think they’re going away just yet, even if businesses may have begun slowly becoming wiser to their threat.

Cointelegraph.com is author of this content, TheBitcoinNews.com is is not responsible for the content of external sites.
Our Social Networks: Facebook Instagram Pinterest Reddit Telegram Twitter Youtube











