Sentinel Protocol is an interactive security threat intelligence platform that combines collective and artificial intelligence (AI) to protect users against hacks and scams.
Within the cryptocurrency sector, reports of scams, hacks, and security threats have literally become the order of the day. Cybercriminals are constantly innovating new ways to breach security walls and this, in turn, stands in the way of mainstream adoption. One of the most highly touted benefits of blockchain technology, decentralization, has also turned into its greatest enemy.
Sentinel Protocol has found a way to turn this weakness into an advantage by creating a decentralized collective intelligence framework. Crypto users acting individually are not able to create a viable solution to this problem. But through this framework, users are able to harness the power of mutual self-interest to address the challenge effectively.
Security Features of the Platform
The Sentinels
At the core of the Sentinel Protocol ecosystem are security professionals known as The Sentinels. These include developers, white hat hackers, security vendors, and professionals. In exchange for their collective intelligence contributions and threat protection innovations, they earn rewards from the platform.
In many cases, ethical white hackers only receive social recognition for their assistance and contributions. But the prospects of getting financial incentives for their efforts offer greater motivation and has created a vibrant community.
The Sentinel Portal
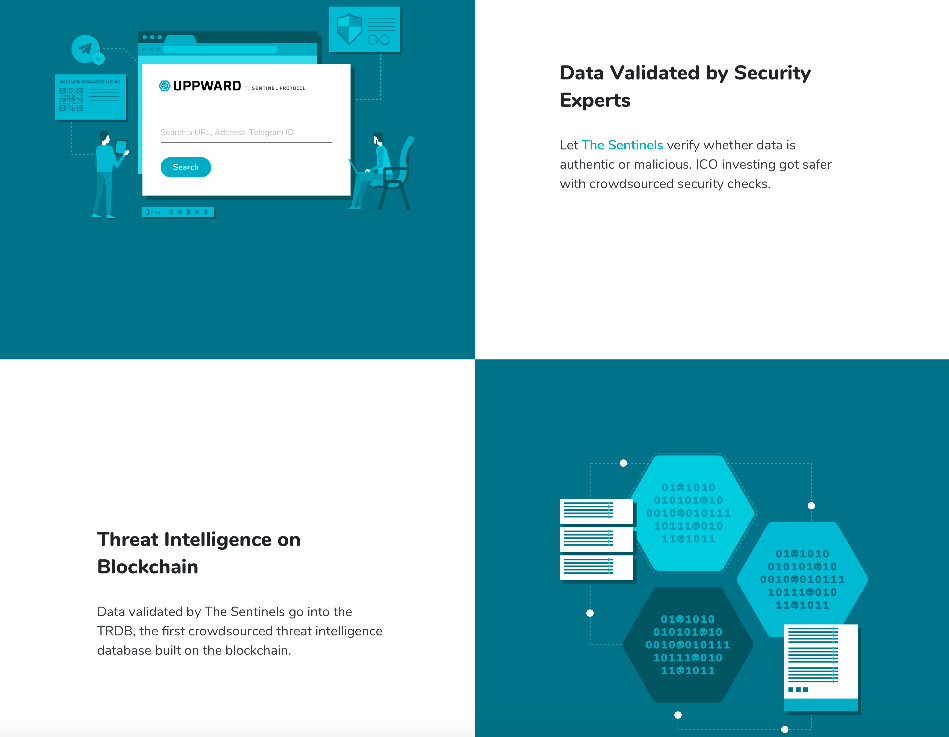
This is an interactive intelligence platform on the ecosystem where The Sentinels validate reported incidents and hacks. Community members also have the opportunity to share news on security issues, insights and tips, and get Sentinel Points in return. Users who are not security experts make manual reports on the system which are later validated by the experts and added to the intelligence platform.
Threat Reputation Database (TRDB)
The TRDB is a blockchain-based reputation system on the Sentinel Protocol. First, by virtue of its decentralization, it eliminates the threat posed by keeping threat data in one central location. As such, the database is not vulnerable to abuse or manipulation.
Secondly, the TRDB addresses the absence of shared knowledge among crypto security vendors. Presently, most existing security vendors compile their own data and store it within walled gardens since there is no incentive for collaboration. But on this framework, it is not a winner takes all game. The more information collected on existing threats, the higher the chances of cyber-crime prevention. Vendors and security experts within this ecosystem are encouraged to make contributions to the database.
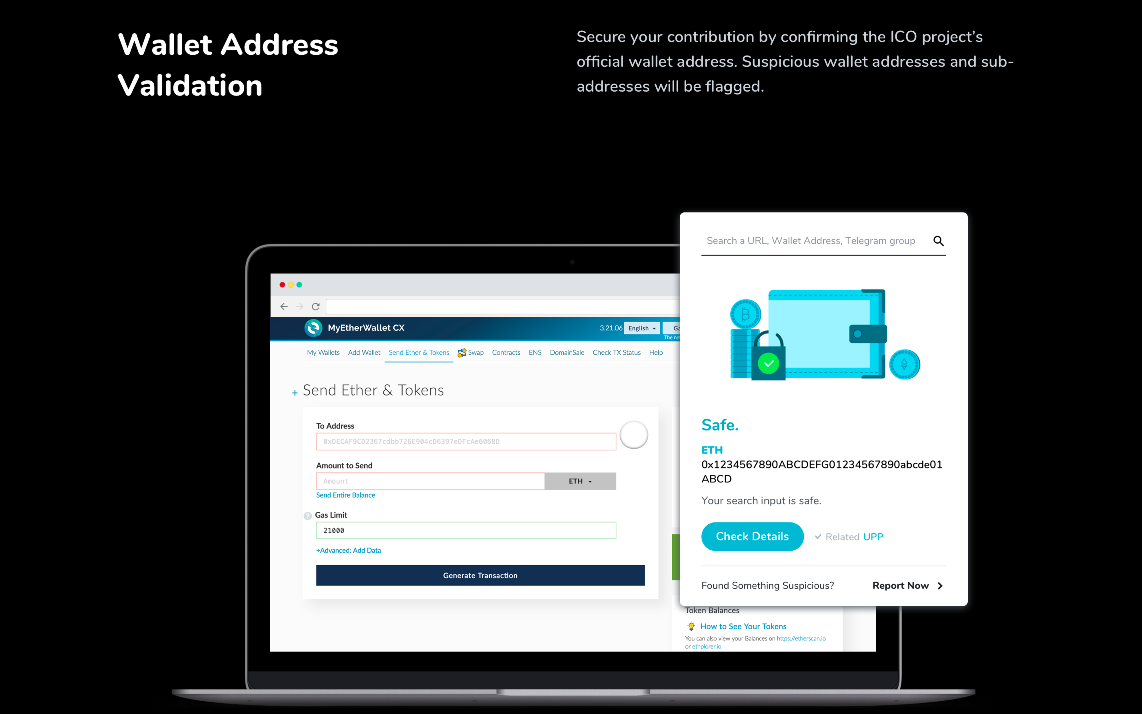
As such, the TRDB is able to effectively collect data on hackers’ wallet addresses, phishing addresses, malware hashes and malicious URLs among others. And even though general users can participate, only security experts update the records to eliminate systemic errors. Through this database, any digital assets acquired through malicious acts are tracked to receiving addresses and sub-addresses. All platforms integrated with Sentinel Protocol are alerted, cutting off any chances of the scammer using the seized assets.
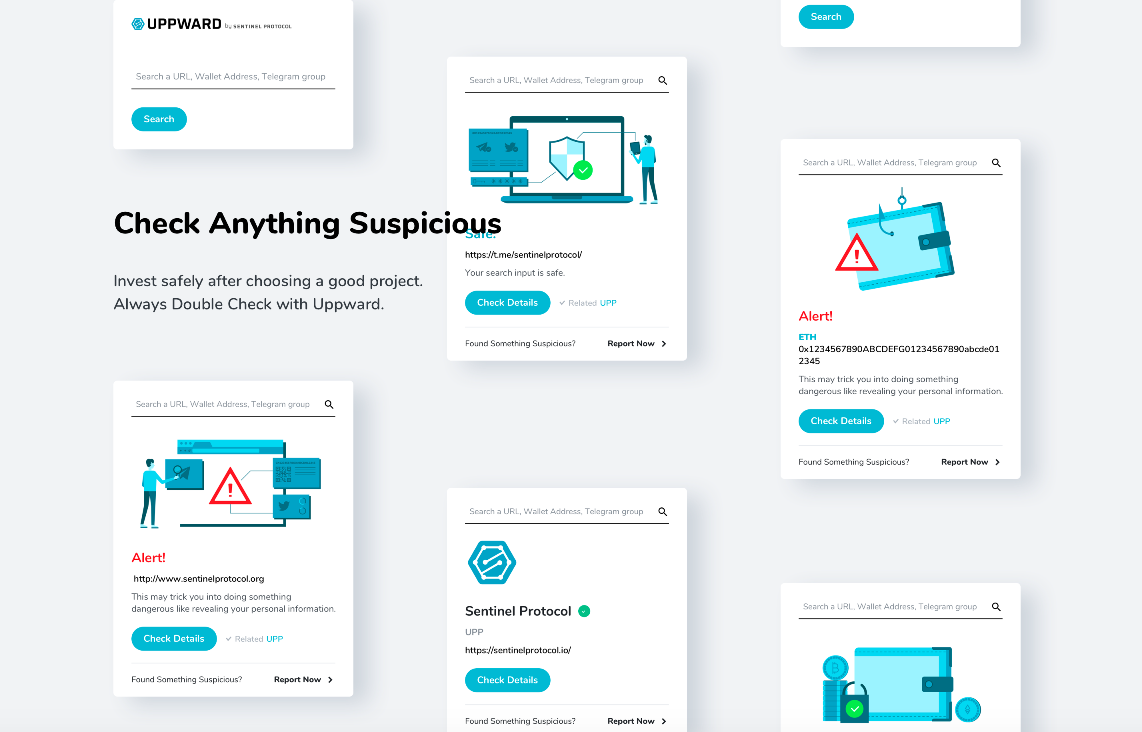
Uppward Chrome Extension
Fake ICO websites have become one of the most common approaches used by malicious actors. For this reason, the Sentinel Protocol has created a security system that investors can use to avert this risk. Uppward Chrome Extension allows platform users to confirm the authenticity of ICO websites, wallet addresses and social media accounts used by ICO projects. By using this protective feature, ICO investors ensure that their contributions go to the right project addresses.
Machine Learning Security Technology
Sentinel Protocol makes use of machine learning to keep track of behavior changes. For starters, it collects existing data and creates model behavior of all normal activities. If at any time this system detects a change in the norm, then it reports the probability of a threat based on the suspicious activity. This could be related to changes in computer usage or transaction patterns among other things. When this happens, the system blocks the execution of the suspicious process and shares the data with the reputation system for further investigation.
Distributed Malware Analysis Sandbox (D-Sandbox)
This feature of the platform makes it possible to run unverified code and programs in a secure environment where they do not pose any risk to the host. Platform users submit threats to this sandbox for analysis by the collective intelligence system.
As hacking and fraud become prevalent in the crypto industry, there is a growing need for a security framework that can cultivate investor and stakeholder trust. Sentinel Protocol provides precisely that, making it possible to reduce hacking and scam incidents significantly. Through its collective intelligence system, threat reputation database and data verification model, the platform makes it a lot safer to interact with blockchains.
Disclaimer: This article should not be taken as, and is not intended to provide, investment advice. Global Coin Report and/or its affiliates, employees, writers, and subcontractors are cryptocurrency investors and from time to time may or may not have holdings in some of the coins or tokens they cover. Please conduct your thorough research before investing in any cryptocurrency and read our full disclaimer.
The post Sentinel Protocol – Protecting Against Crypto Fraud appeared first on Global Coin Report.
Read more at https://globalcoinreport.com/sentinel-protocol-protecting-against-crypto-fraud/

Globalcoinreport.com/ is author of this content, TheBitcoinNews.com is is not responsible for the content of external sites.
Our Social Networks: Facebook Instagram Pinterest Reddit Telegram Twitter Youtube