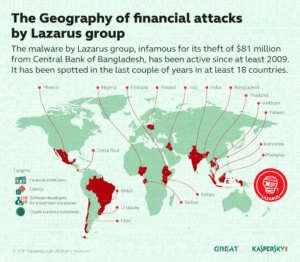
A new report from Kaspersky Labs reveals that North Korean hackers are now using their ‘Lazarus’ trojan to hack cryptocurrency traders and exchanges.
Typically used for conducting political interference, “Lazarus has been a major threat actor in the APT arena for several years,” Securelist reports. “Alongside goals like cyberespionage and cybersabotage, the attacker has been targeting banks and other financial companies around the globe. Over the last few months, Lazarus has successfully compromised several banks and infiltrated a number of global cryptocurrency exchanges and fintech companies.”
The hackers behind Lazarus are now lacing their malware into professional-looking cryptocurrency trading software typically being sent to crypto users over email.
Kaspersky Lab has been investigating Lazarus for over a year. In 2016, the Lazarus group attempted to steal $851 million from the Central Bank of Bangladesh for which they successfully collected $81 million.
According to the report,
“Kaspersky Lab has been assisting with incident response efforts. While investigating a cryptocurrency exchange attacked by Lazarus, we made an unexpected discovery. The victim had been infected with the help of a trojanized cryptocurrency trading application, which had been recommended to the company over email. It turned out that an unsuspecting employee of the company had willingly downloaded a third-party application from a legitimate looking website and their computer had been infected with malware known as Fallchill, an old tool that Lazarus has recently switched back to. There have been multiple reports on the reappearance of Fallchill, including one from US-CERT.”
What’s even more troubling is that the hackers have now developed malware for multiple OS platforms including macOS. This is a first for the Lazarus group, and their website states that a Linux version is currently under development.
“The fact that the Lazarus group has expanded its list of targeted operating systems should be a wake-up call for users of non-Windows platforms,” the Securelist report warns.
Lazarus Could Be Raising Hell in Crypto
The Lazarus Trojan has been detected in a third-party cryptocurrency trading program called Celas Trade Pro. Upon download, there is nothing suspicious about the the all-in-one trading software. However, once installed, Lazarus begins to load the malware suite ‘Fallchill’ designed to open a series of backdoors which give remote controlled access to the hackers.
“What’s interesting here is that this doesn’t appear to be an attempt to steal cryptocurrency directly,” reports Hard Fork. “Instead, the hackers appear to be looking to disrupt supply chains and businesses in any way they can. Or in this case, by leveraging the increased popularity of cryptocurrency trading. If people in positions of power download the software, the integrity of their businesses would become but a plaything for Lazarus.”
The Mystery of Celas Limited
The report concludes by disclosing the information it has on the mysterious Celas company responsible for the trojanized crypto trading application:
“The website had a valid SSL certificate issued by Comodo CA. However, note that the certificate from this webserver mentions ‘Domain Control Validated’, which is a weak security verification level for a webserver. It does not mean validation of the identity of the website’s owner, nor of the actual existence of the business. When certification authorities issue this kind of certificate they only check that the owner has a certain control over the domain name, which can be abused in certain ways.”
Further analysis revealed that the domain was registered to someone named ‘John Broox’, email address ‘[email protected]’.
Suspiciously, the domain celasslc.com was the only domain registered to this address, and the Kaspersky report reveals that the John Broox email address was exclusively used for this purpose.
John Broox appears to have paid for the domain using cryptocurrency through a site called Domain4Bitcoins. When Kaspersky Labs traced John Broox’s address, they were led to a Ramen noodle shop in Chicago.
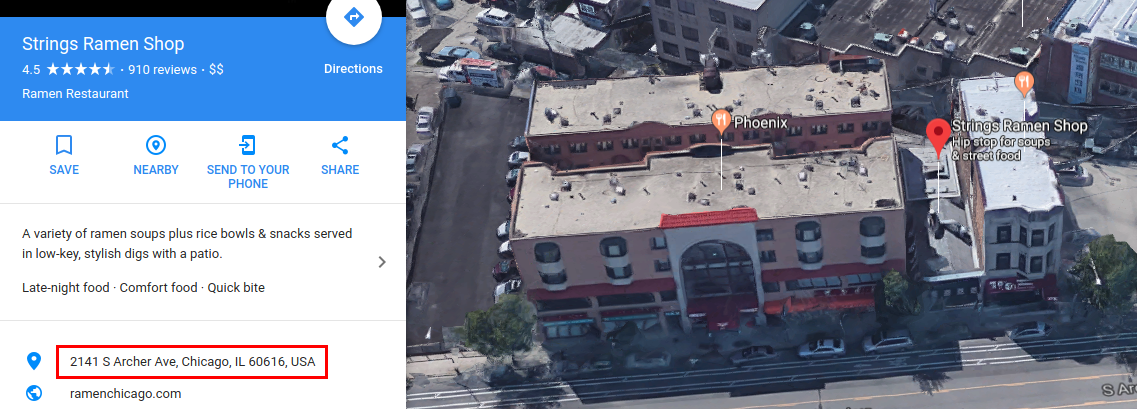
“Coincidentally, the Fallchill malware authors also preferred to use the same hosting company to host their C2 server. Moreover, the Celas LLC web server and one of the C2 servers of the Fallchill malware are located in the same network segment of this ISP.”
Even further analysis revealed that the address of the company included in Celas Trading Pro’s application digital signature traces back to what appears to be an open meadow in a small forest.

Conclusions
While Kaspersky Labs reports that it can’t know for sure if the entire Celas operation was put in place to spread the Lazarus trojan, the company has issued a warning to all crypto traders considering using third party applications:
“This should be a lesson to all of us and a wake-up call to businesses relying on third-party software. Do not automatically trust the code running on your systems. Neither good looking website, nor solid company profile nor the digital certificates guarantee the absence of backdoors. Trust has to be earned and proven. Stay safe!”

Unhashed.com is author of this content, TheBitcoinNews.com is is not responsible for the content of external sites.
Our Social Networks: Facebook Instagram Pinterest Reddit Telegram Twitter Youtube










