Verge Attack
On April 4th, 2018, Verge, formerly known as DogecoinDark, suffered a unique 51% network attack, resulting in someone mining 1560 XVG every second for 3 hours. Typically, a 51% attack requires creating a massive amount of hash power and overwhelming the network. However, in this case, the attacker decided to work smarter, not harder.
To understand the attack, you must first know that XVG uses multi-algorithm consensus. Verge mining cycles through Scrypt, X17, Lyra2rev2, myr-groestl, and blake2s algorithms. If a block is mined with Scrypt, a certain amount of time must pass until Scrypt is allowed again. However, blocks submitted with fake timestamps fooled the network, allowing a miner to use the Scrypt algorithm repeatedly.
When the miner submitted mined blocks, s/he spoofed their timestamps, making it seem like an hour had passed since their inclusion on the network. This allowed the hacker to continue using Scrypt on the next block. The honest miners would have switched to a different algorithm once they saw the block was mined with Scrypt, allowing the malicious miner to continue working with Scrypt, controlling all of the hash power and mining blocks every single second.
Fake Timestamps
Take a look at the block information below to see the beginning of the attack. The timestamps are in bold for you to see the mining of a block per second and the second block with the fake time.
SetBestChain: new best=00000000049c2d3329a3 height=2009406 trust=2009407 date=04/04/18 13:50:09
ProcessBlock: ACCEPTED (scrypt)
—
SetBestChain: new best=000000000a307b54dfcf height=2009407 trust=2009408 date=04/04/18 12:16:51
ProcessBlock: ACCEPTED (scrypt)
—
SetBestChain: new best=00000000196f03f5727e height=2009408 trust=2009409 date=04/04/18 13:50:10
ProcessBlock: ACCEPTED (scrypt)
—
This process continued for 3 hours with over a million dollars of Verge eventually stolen and moved to exchanges.
Verge’s Response
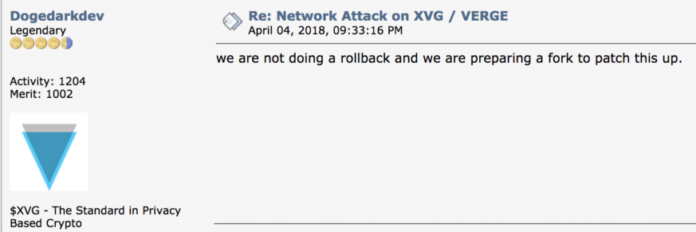
The Verge team eventually sprung into action by copying a commit to Peercoin from 3 years ago to try to stop the attack. You can see the Peercoin commit here and Verge’s here. There are still skeptics that believe this update will be insufficient to stop future attacks.
Verge also reached out on twitter about the debacle.
We had a small hash attack that lasted about 3 hours earlier this morning, it’s been cleared up now. We will be implementing even more redundancy checks for things of this nature in the future! $XVG #vergefam
— vergecurrency (@vergecurrency) April 4, 2018
By “cleared up,”they meant implementing a ‘fix’ that actually hard-forked the blockchain. Another fork is planned for the near future with an update for “extra block verifications.” If you are holding XVG, we recommend not moving them around until this is all sorted out. A Verge developer confirmed the hard fork in an online forum.
This code exploit isn’t coming at a convenient time for Verge, which recently completed a fundraising event to obtain enough coins for a so-called secret partnership. The #vergefam put a lot of faith in the developers, but thus far, have not been rewarded. The announcement for the “largest partnership in crypto to date” is still scheduled for April 17th.
Our deepest gratitude to #vergefam for helping us to achieve this partnership! As you know, we’ve launched a donation rewards program in effort to reward all of those that helped make this happen. Go to our dedicated page https://t.co/ix7A5AcQtK to submit your contribution! pic.twitter.com/5rfA6s0NLG
— vergecurrency (@vergecurrency) April 3, 2018
While there are certain publications out there criticizing the safety of proof of work, it’s important to note that this was not a typical 51% attack. Trying to amass sufficient mining power to attack Bitcoin with a 51% attack is still almost logistically impossible. This attack was unique to Verge’s codebase and a bug related to timestamps. The question remains, is Verge on the verge precipice of collapse or will their developers overcome these technical challenges? While many see this attack as a positive event, strengthening the Verge codebase, it’s important to remember that it’s a doge eat doge world out there.
The post Verge Suffers 51% Attack, Hard Forks in Response appeared first on CoinCentral.

Coincentral.com is author of this content, TheBitcoinNews.com is is not responsible for the content of external sites.
Our Social Networks: Facebook Instagram Pinterest Reddit Telegram Twitter Youtube











